Originally posted 31 March 2025 – Cybercriminals are winning—cybersecurity must strike back now
Key Takeaways
- Cybercriminals are using AI and social engineering to launch more sophisticated attacks.
- Rapid detection is critical—some breaches escalate in under a minute.
- High-profile cyber-attacks are exposing geopolitical risks, from election interference to government breaches.
I recently created a website, but soon after launching it, I noticed it wasn’t appearing in Google searches. While researching how to fix this, I received an email with step-by-step instructions on what to do. Nothing about it seemed suspicious—not even the sender’s address. But when I used artificial intelligence (AI) to verify its authenticity, it was flagged as suspicious.
A few years ago, phishing emails had obvious red flags—poor grammar, strange formatting, or sketchy links. Today, with AI-powered tools at their disposal, cybercriminals are far more sophisticated. And if they’re getting smarter, cybersecurity must become smarter still.
The unbearable cost of a data breach
In 2024, the average cost of a data breach soared to nearly $5 million1. And that’s just the average—meaning many breaches resulted in far greater losses. While this number has been rising for years, 2024 saw a sharp uptick, underscoring how the widespread adoption of advanced AI tools is making cybercriminals smarter and attacks more costly than ever.
“Attack speeds could increase up to 100x as threat actors leverage generative AI” – Palo Alto Networks
In many cases, the true cost of a data breach goes beyond dollars and cents—it’s immeasurable. What happens when customer trust in a business’ security is shattered? The reputational damage could be irreversible. What if a hospital is hacked and a life is lost? The stakes couldn’t be higher. That’s why cybersecurity isn’t just a priority—it’s a necessity. And the world is finally waking up to that reality.
Cybercriminals are becoming smarter
442% increase in voice phishing (vishing) in H2 2024 vs H1 2024 | 79% of attacks were malware-free in 2024 (up from 40% in 2019) |
51 seconds Fastest recorded e-crime breakout time | 257 tracked adversaries including 26 new ones in 2024 |
Source: CrowdStrike 2025 Global Threat Report, March 2025.
When cybercriminals compromise a target, their intention is to infiltrate the organisation via a weak link and move deeper into the network. E-crime breakout time refers to how quickly they escalate control—spreading from the initial breach to critical systems, stealing data, disabling security, or deploying ransomware. Some attackers achieve this in under an hour, making rapid detection and response crucial. In 2024, the fastest recorded time attackers were able to do this was 51 seconds2.
Attackers aren’t always relying on emails—the nuisance calls we receive can often be quite nefarious. Vishing (voice phishing) attacks involve cybercriminals using phone calls to impersonate trusted entities, such as banks, government agencies, or service providers, to trick victims into revealing sensitive information or transferring money. These scams have surged dramatically, with a 442% increase in vishing in H2 2024 vs H1 20243, highlighting how criminals are exploiting human trust over the phone to bypass traditional cybersecurity defences.
A few weeks ago, I saw a post on LinkedIn of a man surrounded by police officers. He was telling the story of how he physically hacked into an organisation, walking through security checkpoints, accessing restricted areas, and pushing his luck until he finally got caught. But this wasn’t a real attack—it was a penetration test, a controlled security exercise designed to identify vulnerabilities before actual criminals exploit them. Organisations conduct these tests because hackers are employing increasingly sophisticated social engineering techniques—manipulating people rather than systems—to bypass security and gain access. The threat is growing, with 79% of attacks in 2024 being malware-free, up from 40% in 20194, proving that cybercriminals don’t always need malware when they can simply trick humans into opening the door.
High profile attacks underscore geopolitical risks
At the outset of 2024, concerns about cyber risks in the election year were widespread. While many countries navigated the electoral cycle without major known cyber incidents, Romania’s December presidential election was notably annulled due to allegations of Russian interference. Far-right candidate Calin Georgescu’s unexpected lead in the first round prompted investigations revealing a coordinated online campaign and cyberattacks supporting his candidacy, leading the courts to void the election.
In the same month, the US Treasury Department reported a significant cybersecurity breach attributed to Chinese state-sponsored hackers. The attackers exploited a third-party software provider to access Treasury workstations and unclassified documents. The breach involved the theft of a security key, allowing remote access to the department’s systems. Although China’s foreign ministry denied these allegations, the incident underscores the growing intersection of geopolitical and cybersecurity risks.
Executives are concerned about risks from AI
A recent World Economic Forum survey5 of executives revealed that 66% believe AI and machine learning will have the biggest impact on cybersecurity in the next 12 months. Yet, 63% admitted their organisations lack processes to assess the security of AI tools before deploying them—highlighting a critical gap between innovation and risk management.
Figure 1: In your view, which of the following will most significantly affect cybersecurity in the next 12 months?
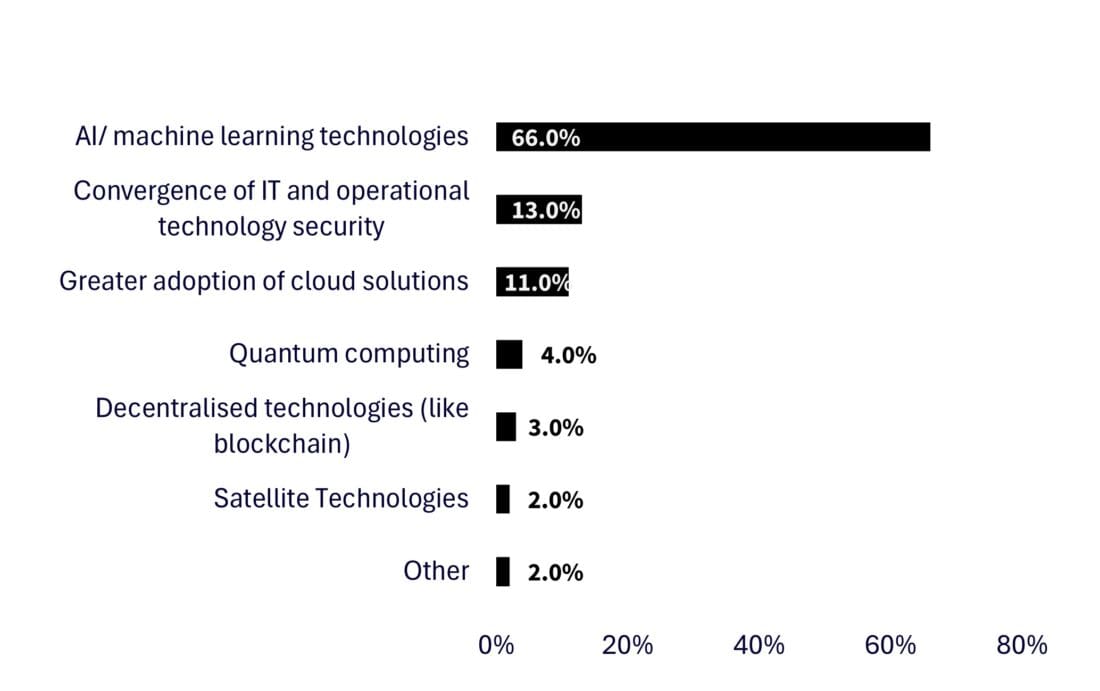
Source: World Economic Forum, Global Cybersecurity Report 2025.
Figure 2: Does your organisation have a process in place to assess the security of AI tools before deploying them?
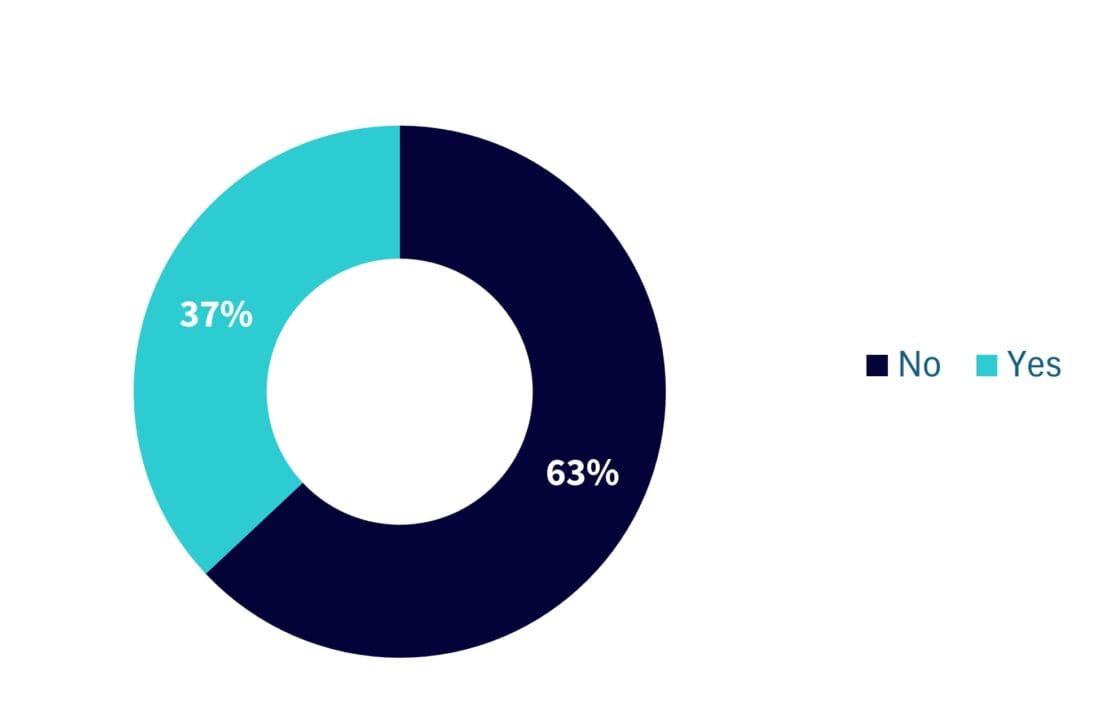
Source: World Economic Forum, Global Cybersecurity Report 2025.
Cybersecurity must stay one step ahead
Cybersecurity must constantly innovate, leveraging cutting-edge technology to stay one step ahead of evolving threats. This relentless race between defenders and attackers is what makes cybersecurity such an exciting and dynamic field. Recent headlines around quantum computing suggest that the age of quantum might be closer than we once thought—a future where a quantum computer could shatter even the most sophisticated encryption effortlessly. This would redefine cybersecurity as we know it. Whether it’s quantum computing, AI, or blockchain, every breakthrough introduces new vulnerabilities, and safeguarding them must be a proactive pursuit, not a reactive one. Because if we wait until the attack happens, it might already be too late.
1 IBM, 2025.
2 Source: CrowdStrike 2025 Global Threat Report, March 2025.
3 Source: CrowdStrike 2025 Global Threat Report, March 2025.
4 Source: CrowdStrike 2025 Global Threat Report, March 2025.
5 Source: World Economic Forum, Global Cybersecurity Report 2025.
Disclosure: WisdomTree Europe
This material is prepared by WisdomTree and its affiliates and is not intended to be relied upon as a forecast, research or investment advice, and is not a recommendation, offer or solicitation to buy or sell any securities or to adopt any investment strategy. The opinions expressed are as of the date of production and may change as subsequent conditions vary. The information and opinions contained in this material are derived from proprietary and non-proprietary sources. As such, no warranty of accuracy or reliability is given and no responsibility arising in any other way for errors and omissions (including responsibility to any person by reason of negligence) is accepted by WisdomTree, nor any affiliate, nor any of their officers, employees or agents. Reliance upon information in this material is at the sole discretion of the reader. Past performance is not a reliable indicator of future performance.
Please click here for our full disclaimer.
Jurisdictions in the European Economic Area (“EEA”): This content has been provided by WisdomTree Ireland Limited, which is authorised and regulated by the Central Bank of Ireland.
Jurisdictions outside of the EEA: This content has been provided by WisdomTree UK Limited, which is authorised and regulated by the United Kingdom Financial Conduct Authority.
Disclosure: Interactive Brokers Third Party
Information posted on IBKR Campus that is provided by third-parties does NOT constitute a recommendation that you should contract for the services of that third party. Third-party participants who contribute to IBKR Campus are independent of Interactive Brokers and Interactive Brokers does not make any representations or warranties concerning the services offered, their past or future performance, or the accuracy of the information provided by the third party. Past performance is no guarantee of future results.
This material is from WisdomTree Europe and is being posted with its permission. The views expressed in this material are solely those of the author and/or WisdomTree Europe and Interactive Brokers is not endorsing or recommending any investment or trading discussed in the material. This material is not and should not be construed as an offer to buy or sell any security. It should not be construed as research or investment advice or a recommendation to buy, sell or hold any security or commodity. This material does not and is not intended to take into account the particular financial conditions, investment objectives or requirements of individual customers. Before acting on this material, you should consider whether it is suitable for your particular circumstances and, as necessary, seek professional advice.













Join The Conversation
If you have a general question, it may already be covered in our FAQs page. go to: IBKR Ireland FAQs or IBKR U.K. FAQs. If you have an account-specific question or concern, please reach out to Client Services: IBKR Ireland or IBKR U.K..
Visit IBKR U.K. Open an IBKR U.K. Account